![PDF] Security Architecture Design for Satellite Aeronautical Data Link Communications | Semantic Scholar PDF] Security Architecture Design for Satellite Aeronautical Data Link Communications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5572cda9168d7fb5105cc42bb630e6d69fb1fc2e/5-Figure2-1.png)
PDF] Security Architecture Design for Satellite Aeronautical Data Link Communications | Semantic Scholar

In-depth Overview of Network Security Features for Cisco Integrated Services Routers Generation 2 - Cisco
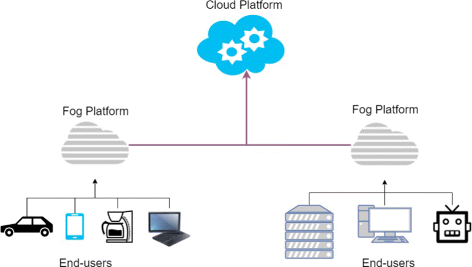
Fog computing security: a review of current applications and security solutions | Journal of Cloud Computing | Full Text

Router Security Strategies Securing IP Network Traffic Planes – Networking Book PDF Book | Free PDF Books